Today, we’re pleased to announce Cover Your Tracks, the newest edition and rebranding of our historic browser fingerprinting and tracker awareness tool Panopticlick. Cover Your Tracks picks up where Panopticlick left off. Panopticlick was about letting users know that browser fingerprinting was possible; Cover Your Tracks is about giving users the tools to fight back against the trackers, and improve the web ecosystem to provide privacy for everyone.
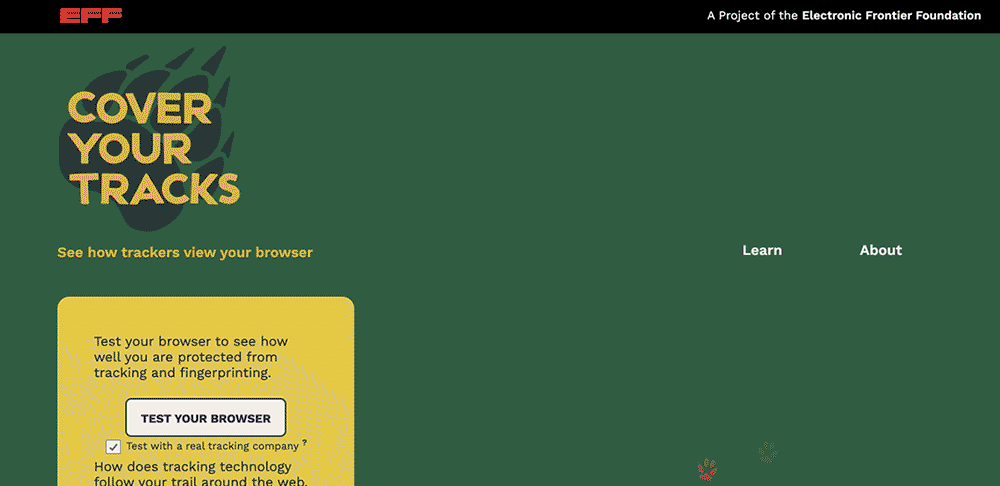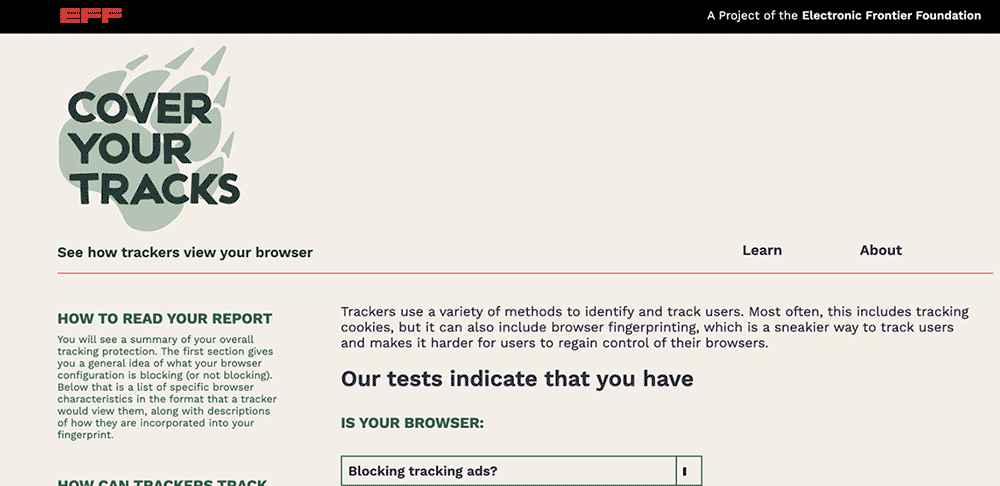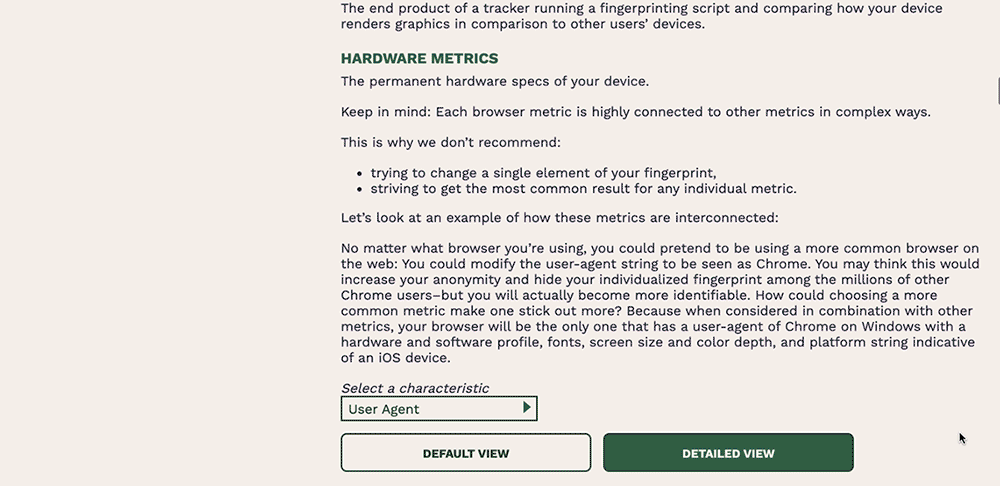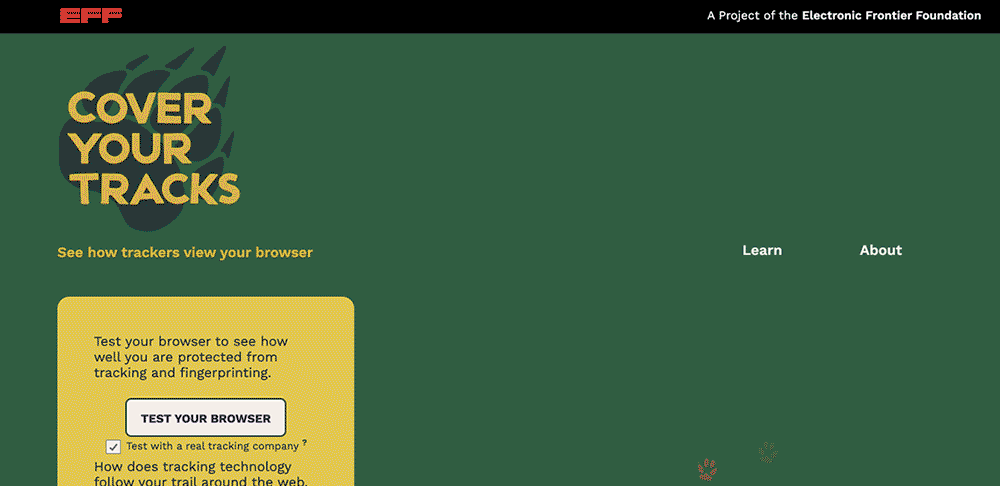
A screen capture of the front page of coveryourtracks.eff.org. The mouse clicks on “Test your browser” button, which loads a results page with a summary of protections the browser has in place against fingerprinting and tracking. The mouse scrolls down to toggle to “detailed view”, which shows more information about each metric, such as further information on System Fonts, Language, and AudioContext fingerprint, among many other metrics.
Over a decade ago, we launched Panopticlick as an experiment to see whether the different characteristics that a browser communicates to a website, when viewed in combination, could be used as a unique identifier that tracks a user as they browse the web. We asked users to participate in an experiment to test their browsers, and found that overwhelmingly the answer was yes—browsers were leaking information that allowed web trackers to follow their movements.

The old Panopticlick website.
In this new iteration, Cover Your Tracks aims to make browser fingerprinting and tracking more understandable to the average user. With helpful explainers accompanying each browser characteristic and how it contributes to their fingerprint, users get an in-depth look into just how trackers can use their browser against them.
Our browsers leave traces of identifiable information just like an animal might leave tracks in the wild. These traces can be combined into a unique identifier which follows users’ browsing of the web, like wildlife which has been tagged by an animal tracker. And, on the web and in the wild, one of the best ways to confuse trackers and make it hard for them to identify you individually. Some browsers are able to protect their users by making all instances of their browser look the same, regardless of the computer it’s running on. In this way, there is strength in numbers. Users can also “cover their tracks, ” protecting themselves by installing extensions like our own Privacy Badger.

A screenshot from Cover Your Tracks’ learning page, https://coveryourtracks.eff.org/learn
For beginners, we’ve created a new learning page detailing the methodology we use to mimic trackers and test browsers, as well as next steps users can take to learn more and protect themselves. Because tracking and fingerprinting are so complex, we wanted to provide users a way to deep-dive into exactly what kind of tracking might be happening, and how it is performed.
We have also worked with browser vendors such as Brave to provide more accurate results for browsers that are employing novel anti-fingerprinting techniques. Add-ons and browsers that randomize the results of fingerprinting metrics have the potential to confuse trackers and mitigate the effects of fingerprinting as a method of tracking. In the coming months, we will provide new infographics that show users how they can become safer by using browsers that fit in with large pools of other browsers.
We invite you to test your own browser and learn more – just head over to Cover Your Tracks!
