Hundreds of millions of phone numbers linked to Facebook accounts have been found online.
The exposed server contained more than 419 million records over several databases on users across geographies, including 133 million records on U.S.-based Facebook users, 18 million records of users in the U.K., and another with more than 50 million records on users in Vietnam.
But because the server wasn’t protected with a password, anyone could find and access the database.
Each record contained a user’s unique Facebook ID and the phone number listed on the account. A user’s Facebook ID is typically a long, unique and public number associated with their account, which can be easily used to discern an account’s username.
But phone numbers have not been public in more than a year since Facebook restricted access to users’ phone numbers.
TechCrunch verified a number of records in the database by matching a known Facebook user’s phone number against their listed Facebook ID. We also checked other records by matching phone numbers against Facebook’s own password reset feature, which can be used to partially reveal a user’s phone number linked to their account.
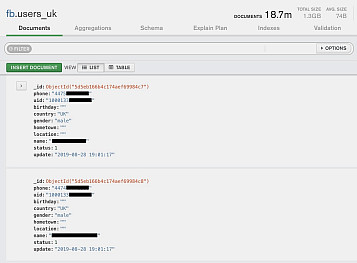
Some of the records also had the user’s name, gender and location by country.
A redacted set of records from the U.K. database. The “44” indicates +44, the U.K.’s country code and the “7” indicates a cell phone number.
This is the latest security lapse involving Facebook data after a string of incidents since the Cambridge Analytica scandal, which saw more than 80 million profiles scraped to help identify swing voters in the 2016 U.S. presidential election.
Since then the company has seen several high-profile scraping incidents, including at Instagram, which recently admitted to having profile data scraped in bulk.
This latest incident exposed millions of users’ phone numbers just from their Facebook IDs, putting them at risk of spam calls and SIM-swapping attacks, which relies on tricking cell carriers into giving a person’s phone number to an attacker. With someone else’s phone number, an attacker can force-reset the password on any internet account associated with that number.
Sanyam Jain, a security researcher and member of the GDI Foundation, found the database and contacted TechCrunch after he was unable to find the owner. After a review of the data, neither could we. But after we contacted the web host, the database was pulled offline.
Jain said he found profiles with phone numbers associated with several celebrities.
Facebook spokesperson Jay Nancarrow said the data had been scraped before Facebook cut off access to user phone numbers.
“This data set is old and appears to have information obtained before we made changes last year to remove people’s ability to find others using their phone numbers, ” the spokesperson said. “The data set has been taken down and we have seen no evidence that Facebook accounts were compromised.”
But questions remain as to exactly who scraped the data, when it was scraped from Facebook and why.
Facebook has long restricted developers‘ access to user phone numbers. The company also made it more difficult to search for friends’ phone numbers. But the data appeared to be loaded into the exposed database at the end of last month — though that doesn’t necessarily mean the data is new.
This latest data exposure is the most recent example of data stored online and publicly without a password. Although often tied to human error rather than a malicious breach, data exposures nevertheless represent an emerging security problem.
In recent months, financial giant First American left data exposed, as did MoviePass and the Senate Democrats.